Generate a Request for an X.509 Certificate
Notes:
The Windows certificate store has two locations: one is per-user (the Current User store) and other, per-machine (the Local Computer store). When you generate the certificate request, it is held in the per-user store for the user making the certificate request.
When the certificate comes back from the CA, it is processed by associating it with the original request. As the original request is held in the Current User store, this processing must be done by the same user who made the certificate request, on the same computer as the request was made on.
The completed certificate must then be moved from the per-user store to the per-machine store.
You must use an account in the local administrators group, as access to the per-machine store is restricted. If your site follows good security management procedures, this is unlikely to be either your personal account, or the account under which VTScada is running.
Those who ignore this warning typically fail to complete the process of requesting and processing an X.509 certificate.
- Choose a Certificate Authority such as Thawte, VeriSign, GoDaddy or other.
- Open a web browser to their page related to purchasing a certificate.
This will have pricing and instructions for certificate options. Leave the page open while continuing with these steps. - Open the VTScada Application Manager (VAM)
- Expand the menu and select the VTScada Thin Client/Server Setup option.
The VTScada Thin Client/Server Setup dialog opens.
- Click the X.509 Certificate tab. The dialog appears as shown.
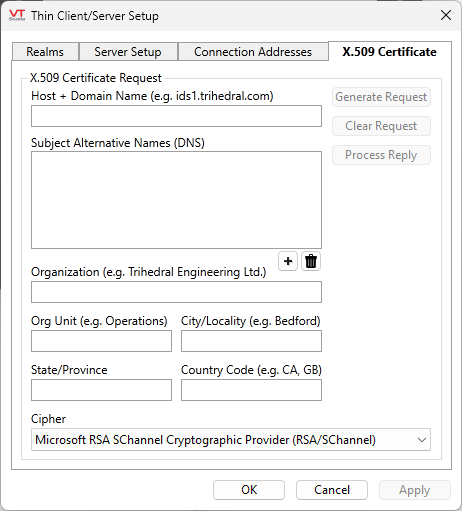
- Enter the host and domain name in the Host + Domain Name field.
The name you supply must exactly match the host + domain name supplied in the URL used to access the VTScada Thin Client Server. For example:
myserver.trihedral.com
Where, "myserver.trihedral.com" is the host + domain name, "myserver" being the host, and "trihedral.com" being the domain name. You may also use a wildcard, if applicable to your situation:
*.trihedral.com
- Enter the Subject Alternative Names (DNS) using the + button below the field.
Clicking the + button creates a data input field within the SAN block as shown:
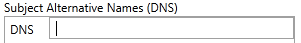 The field accepts a fully qualified domain name (FQDN). We only support DNS entries in the SAN fields.
The field accepts a fully qualified domain name (FQDN). We only support DNS entries in the SAN fields.
- Enter the name of your organization in the Organization field.
- Fill in the remaining identifying fields.
- Select the cipher you wish to use for cryptography from the Cipher drop-down list.
Note that there is normally only one cipher ("Microsoft RSA SChannel Cryptographic Provider (RSA/SChannel)") available for selection, unless you have installed a custom cryptographic package.
After all fields have been entered, the Generate Request button becomes enabled.
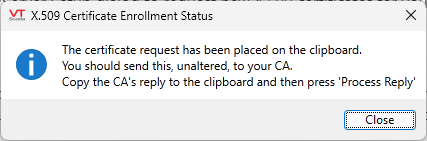
- Click the Generate Request button.
VTScada compiles the data you've entered and displays the following dialog:
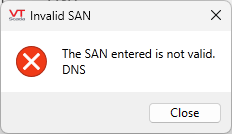
If the request failed, the Enrollment Status dialog will display an error message relevant to the problem. For example:
- If your chosen Certificate Authority has an online form, paste (Ctrl + V) the clipboard contents into the appropriate field of that form.
- Otherwise - - Open the text editor of your choice (Notepad, UltraEdit.) Paste (Ctrl + V) the certificate request into your text editor.
The pasted request begins with "-----BEGIN CERTIFICATE REQUEST-----" and ends with "-----END CERTIFICATE REQUEST-----". - Save the text file.
- Send the text file to your Certificate Authority.
When VTScada generates the certificate request, a matching public/private key pair is generated. The public key is encoded into the certificate request and is sent to the CA. The private key is placed in a secure, encrypted key store. If you do not take a backup of your private key, a system restore operation or catastrophic computer failure will cause loss of the private key. This will require that you generate a new key and a new request. Therefore, it is highly recommended that you use the Microsoft Management Console (MMC) to backup the certificate request and private key. After you receive your certificate and subsequently process it, you should again do a backup using MMC.
After you generate the certificate, do not use Clear Response. Process the response. The data will still be in the boxes. When you need to renew the certificate, you can generate a new request from the data already there.
Use Clear Response only when you need to change a parameter and generate a new request.
